January 7th, 2014 at 11:01 am
 Hello everyone,
Hello everyone,
In this March post I told you about three great programs that will show you all of your computers third party program vulnerabilities, and then download and install the latest vulnerability fixes. Great stuff!
Speaking of vulnerabilities, here is a chart of the non-MS patches that affected Windows platforms in the past month of December 2013. Get updated asap!
|
Identifier
|
Vendor/Product
|
Product Version Affected
|
Date Released by Vendor
|
Vulnerability Info
|
Vendor
Severity / My Recommendation
|
|
APSB13-28
|
Adobe Flash Player
|
Windows/Mac 11.9.900.152 and earlier Linux 11.2.202.327 and earlier
|
12/10/2013
|
Arbitrary Code Execution or Denial of Service
|
Critical: Priority 1/ Upgrade within 72 hours if possible
|
|
APSB13-28
|
Adobe Air
|
Windows/Mac/Android 3.9.0.1210 and earlier
|
12/10/2013
|
Remote Code Execution or Denial of Service
|
Critical: Priority 3 (upgrade at admin’s discretion)
|
|
APSB13-29
|
Adobe Shockwave Player
|
Windows/Mac 12.0.6.147 and earlier
|
12/10/2013
|
Arbitrary Code Execution or Denial of Service
|
Critical: Priority 1/ upgrade within 72 hours
|
|
6.1.1/7.0.1
|
Apple Safari
|
Safari 6.1.1 and 7.0.1
|
12/16/2013
|
Arbitrary Code Execution, Denial of Service, and credential disclosure
|
Critical: Upgrade to latest release
|
|
26/ESR 24.2
|
Firefox
|
Before Firefox 26 and ESR 24.2
|
12/10/2013
|
Denial of Service, Arbitrary Code Execution, Cross Site Scripting, Security Control Bypass
|
Critical: Upgrade to latest release
|
|
24.2
|
Thunderbird
|
Before 24.2
|
12/10/2013
|
Arbitrary Code Execution, Denial of Service
|
Critical: Upgrade to latest release
|
|
2.23
|
Seamonkey
|
Before 2.23
|
12/10/2013
|
Arbitrary Code Execution, Denial of Service, Security Control Bypass,
|
Critical: Upgrade to latest release
|
|
31.0.1650.63
|
Chrome
|
Before 31.0.1650.63
|
12/4/2013
|
Denial of Service, Web Session Hijack, AddressBar Spoofing
|
Recommended: Upgrade after testing
|
|
17.0.4.61
|
RealPlayer
|
Before 17.0.4.61
|
12/20/2013
|
Arbitrary Code Execution
|
Critical: Upgrade to latest release
|
Best wishes,
Randy The Tech Professor
Tags:
critical third party (non microsoft) upgrades,
patch third party programs,
third party program update for December 2013
December 17th, 2013 at 8:47 pm
 Hello everyone,
Hello everyone,
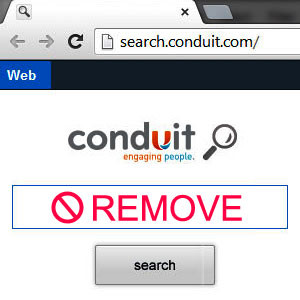
A while back in this post I wrote about the plague of malicious toolbars, browser hijackers, browser add-ons, and browser extensions. One of the most prominent of these insidious, unwanted programs is a little gem called Conduit.
Conduit is a browser hijacker, which is promoted via other free downloads, and once installed will add the Conduit Toolbar which will change your browser homepage and default search engine to search.conduit.com.
Conduit Search will display advertisements and sponsored links in your search results, and may collect search terms from your search queries. The Conduit infection is used to boost advertising revenue, as in the use of blackhat SEO, to inflate a site’s page ranking in search results.
Conduit it’s technically not a virus, but it does exhibit plenty of malicious traits, such as rootkit capabilities to hook deep into the operating system, browser hijacking, and in general just interfering with the user experience. The industry generally refers to it as a “PUP,” or potentially unwanted program.
Many times after I remove Conduit, I get the following RunDLL “Error loading…” message on boot up:
c:\users\ed\appData\local\conduit\backgroundcontainer\background container.dll
This is because a Conduit orphaned registry entry still remains (even after removal), and is telling Windows to load the file upon boot up.
Here is the fix:
1. Go to Start > Control Panel > Administrative Tools.
2. Open Task Scheduler and click on Task Scheduler Library.
3. Look through the list for an entry related to BackgroundContainer.
4. If found, right-click on it and select Delete.
5. Exit all programs and reboot the computer when done.
Professor Randy says: Be extra cautious when downloading third-party browser add-ons, extensions, plugins, toolbars, browser helper objects, and generally most software. Conduit may “come along for the ride”.
Tags:
background container.dll error,
conduit search toolbar,
remove conduit search
November 26th, 2013 at 8:23 pm
Hello everyone,
In this March post I told you about three great programs that will show you all of your computers third party program vulnerabilities, and then download and install the latest vulnerability fixes. Great stuff!
Speaking of vulnerabilities, here is a chart of the non-MS patches that affected Windows platforms in the present month of November 2013. Get updated asap!
|
Identifier
|
Vendor/Product
|
Product Version Affected
|
Date Released by Vendor
|
Vulnerability Info
|
Vendor
Severity / Our Recommendation
|
|
APSB13-26
|
Adobe Flash Player
|
Windows 11.9.900.117 and earlier
|
11/12/2013
|
Remote Code Execution or Denial of Service
|
Critical: Priority 1/ Upgrade within 72 hours if possible
|
|
APSB13-26
|
Adobe Air
|
Windows 3.9.0.1030 and earlier
|
11/12/2013
|
Remote Code Execution or Denial of Service
|
Critical: Priority 3 (upgrade at admin’s discretion)
|
|
APSB13-27
|
Cold Fusion
|
All Platforms Versions 10, 9.0.2, 9.0.1 and 9.0
|
11/12/2013
|
Cross Site Scripting Vulnerability
|
Important: Priority 1/ upgrade within 72 hours
|
|
31.0.1650.57
|
Google Chrome
|
All Platforms before 31.0.1650.57
|
11/14/2013
|
Remote Code Execution or Denial of Service
|
Critical: Upgrade to latest release
|
|
MFSA 2013-103
|
Firefox
|
Before 25.0.1
|
11/15/2013
|
Remote Code Execution or Denial of Service
|
Critical: upgrade to latest release
|
|
MFSA 2013-103
|
Thunderbird
|
Before 24.1.1
|
11/15/2013
|
Remote Code Execution or Denial of Service
|
Critical: upgrade to latest release
|
|
MFSA 2013-103
|
Seamonkey
|
Before 2.22.1
|
11/15/2013
|
Remote Code Execution or Denial of Service
|
Critical: upgrade to latest release
|
Tags:
patch all third party programs,
third party program updates for November 2013
November 2nd, 2013 at 1:54 pm
 Hello everyone,
Hello everyone,
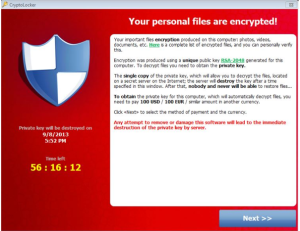
CryptoLocker is an awful virus that an alarming amount of people are falling victim to. It presents itself in the form of an email message that will look familiar and authentic (it will apper as from legitimate businesses and as fake FedEx, DHL, and UPS tracking notifications). This could also be something from a bank or paypal, prompting you to click a link. It may look like a .PDF file, but in reality it’s an executable file that launches the virus.
Once it’s opened, it encrypts all of the documents in your personal “Documents” folder, and can even reach out to files on thumb drives and networks. It uses strong encryption that truly no one can decrypt, and the only way you would be able to get the data back is by paying $300 for the key. If you don’t pay within 72 hours, the virus authors delete the key and the data is gone forever. To make matters worse, law enforcement has been shutting down servers that contain keys. So even if you were to pay within 72 hours, there’s still no guarantee you will be able to get to your data.
CryptoLocker has also managed to get past AntiVirus programs, although there is a free tool that will supposedly prevent its infection. The problem is, if it gets traction, the CryptoLocker virus authors can easily circumvent it making that tool ineffective. It’s very important to be careful when clicking links that are sent to you.
This means backup is more important than ever. However, you have to be careful how you’re backing up also. If you’re backing up to shared network attached storage for example, that may not be enough. If CryptoLocker can see the files, it will encrypt those also. Furthermore, if you don’t catch it right away, you may end up backing up the encrypted files over top of the unencrypted files. It’s important to have a backup system that supports versioning, or something that allows you to roll back to a prior version of your files.
Professor Randy says: The CryptoLocker virus is really nasty! Protect yourself by backing up all data, and by not clicking on e-mail links unless you’re absoleutely sure where they came from!
Tags:
cryptolocker virus
November 2nd, 2013 at 12:37 pm
Hello everyone,
In this March post I told you about a great program that will show you all of your computers third party program vulnerabilities, and then download and install the latest vulnerability fixes. Great stuff!
Speaking of vulnerabilities, here is a chart of the non-MS patches that affected Windows platforms in the past month of October. Get updated asap!
|
Identifier
|
Vendor/Product
|
Product Version Affected
|
Date Released by Vendor
|
Vulnerability Info
|
Vendor
Severity / Our Recommendation
|
|
APSB13-25
|
Adobe Reader and Acrobat XI
|
For Windows, version 11.0.04. Version 10.1.8 and earlier not affected
|
10/8/2013
|
Remote Code – allows remote attackers to execute arbitray code via PDF’s
|
Critical: Priority 2 / upgrade within 30 days
|
|
APSB13-24
|
Adobe Robohelp
|
10 for Windows
|
10/8/2013
|
Remote Code – allows attackers to execute arbitray code or cause DoS
|
Critical: Priority 3 (upgrade at admin’s discretion)
|
|
6.0
|
Apple Keynote
|
OS X Mavericks v10.9 or later
|
10/22/2013
|
Requires physical access to machine. Screen may be unlocked if put to sleep while Keynote is in presentation mode
|
Low: install as needed
|
|
11.1.2
|
Apple iTunes
|
Windows 7, Vista, and XP SP2 or later
|
10/23/2013
|
Possible arbitrary code execution
|
Recommended
|
|
30.0.1599.101
|
Google Chrome
|
Windows, Mac, Linux, and Chrome Frame
|
10/1/2013
|
50+ security vulnerabilities fixed
|
Critical: Includes fixes to High priority bugs. Google recommends letting the browser update automatically.
|
|
30.0.1599.114
|
Google Chrome
|
Linux Only
|
10/22/2013
|
1 bug fix, resolves issues installing x32 version
|
Low: install as needed
|
|
7u45
|
Oracle Java SE, Java FX, Java SE Embedded
|
SE 7u40 and earlier, SE 6u60 and earlier, SE 5.0u51 and earlier, SE Embedded 7u40 and earlier, JavaFX 2.2.40 and earlier
|
10/22/2013
|
50+ security vulnerabilities fixed of which 50 may be remotely exploitable without authentication
|
Critical: upgrade to latest release
|
Best wishes,
Randy The Tech Professor
Tags:
non-microsoft patches for october 2013,
october third party program updates,
third party program updates
October 6th, 2013 at 12:28 pm
Hello everyone,
Note: Part 2 of this post can be found here
In just the past month I have witnessed a veritable plague in my area of computer repair work. Unwanted items are almost secretly installing themselves to the Google Chrome, Mozilla Firefox, and Microsoft Internet Explorer browsers. Many of my great clients are seniors and they are being “suckered” into installing these unwanted programs.
These malicious items cause annoying pop-ups, pop-unders, banners, and coupons. They change Windows start-up settings and Internet browser settings. They change the homepage, redirect browser searches, and generally make Internet browsing experience hell! Ultimately they will ruin the computers functionality!
These vicious little programs primarily bundle with third party software, most often freeware and shareware. Once in a while the user may be given the opportunity to decline the offer to install the “piggyback” item, but many times the offer is presented in a manner that attempts to trick the user. Often these malicious programs will install even if declined!
Here is a list of what I’ve eliminated from ten or so machines in the past month (no particular order):
1) Shop At Home Toolbar
2) Inbox Toolbar
3) Ask Toolbar
4) MapsGalaxy Toolbar
5) CouponBar
6) Babylon Toolbar
7) VAFMusic4 Toolbar
8) Snap.do
9) WebCake
10) Blekko Search Bar
11) Yontoo
12) WebSearch Toolbar
13) Default Tab
14) SaltarSmart
15) Win32/AddLyrics
16) Delta-homes.com (redirect)
In my next post I will explain how to rid your computer of these “plagues”.
Professor Randy says: Certain unfriendly entities want to enter your computer without your knowledge. First, be aware or who/what they are, and second, learn how to protect yourself from them!
Tags:
browser add-ons,
browser extensions,
browser highjackers,
remove unwanted browser add-ons,
toolbars
September 24th, 2013 at 8:44 pm
Hello everyone,
In this March post I told you about a great program that will show you all of your computers third party program vulnerabilities, and then download and install the latest vulnerability fixes. Great stuff!
Speaking of vulnerabilities, here is a chart of the non-MS patches that affect Windows platforms in the present month of September. Get updated asap!
|
Identifier
|
Vendor/Product
|
Product Version Affected
|
Date Released by Vendor
|
Vulnerability Info
|
Vendor
Severity / Our Recommendation
|
|
APSB13-21
|
Adobe Flash Player
|
For Windows,
before 11.8.800.94
|
9/10/2013
|
Multiple vulnerabilities
|
Critical: Priority 1(upgrade within 72 hours)
|
|
APSB13-21
|
Adobe Air
|
For Windows,
before 3.8.0.1433
|
9/10/2013
|
Multiple vulnerabilities
|
Critical: Priority 3 (upgrade at admin’s discretion)
|
|
APSB13-22
|
Adobe Reader and Acrobat
|
For Windows,
before 11.0.4
|
9/10/2013
|
Multiple vulnerabilities
|
Critical: Priority 2 (upgrade within 30 days)
|
|
APSB13-23
|
Adobe Shockwave Player |
For Windows,
before 12.0.3.134 |
9/10/2013
|
Multiple vulnerabilities
|
Critical: Priority 1 (upgrade within 72 hours)
|
|
29.0.1547.76
|
Google Chrome
|
For Windows before
29.0.1547.76
|
9/18/2013
|
No new vulnerability information
|
Google recomends automatic update
|
|
24.0
|
Mozilla Firefox
|
Before 24.0
|
9/17/2013
|
Multiple High risk vulnerabilties fixed
|
Critical: upgrade to latest release
|
|
24.0
|
Mozilla Thunderbird
|
Before 24.0
|
9/17/2013
|
Multiple High risk vulnerabilties fixed
|
Critical: upgrade to latest release
|
|
2.21
|
Mozilla SeaMonkey
|
Before 2.21
|
9/17/2013
|
Multiple High risk vulnerabilties fixed
|
Critical: upgrade to latest release
|
Best wishes,
Randy The Tech Professor
Tags:
third party program updates for September 2013,
unpatched third party apps
August 31st, 2013 at 9:19 pm
Hello everyone,
In this March post I told you about a great program that will show you all of your computers third party program vulnerabilities, and then download and install the latest vulnerability fixes. Great stuff!
Speaking of vulnerabilities, here is a chart of the non-MS patches that affect Windows platforms in the present month of August. Get updated asap!
|
|
|
|
Identifier
|
Vendor/Product
|
Product Version Affected
|
Date Released by Vendor
|
Vulnerability Info
|
Vendor
Severity / Our Recommendation
|
|
APSB13-20
|
Adobe Digital Editions
|
For Windows,
before 2.0.1
|
7/30/2013
|
Memory corruption could allow remote code
|
Critical: Priority 3 (patch at admins’ discretion)
|
|
27.0.1547.57
|
Google Chrome
|
For Windows before
27.0.1547.57
|
7/11/2013
|
Multiple high risk vulnerabilities fixed
|
Critical: upgrade to latest release
|
|
23.0
|
Mozilla Firefox
|
Before 23
|
8/6/2013
|
Multiple High risk vulnerabilties fixed
|
Critical: upgrade to latest release
|
|
17.0.8
|
Mozilla Thunderbird
|
Before 17.0.8
|
8/6/2013
|
Multiple High risk vulnerabilties fixed
|
Critical: upgrade to latest release
|
|
2.20
|
Mozilla SeaMonkey
|
Before 2.20
|
8/6/2013
|
Multiple High risk vulnerabilties fixed
|
Critical: upgrade to latest release
|
Tags:
app updates for August 2013,
patch third party program
July 25th, 2013 at 3:15 pm
Hello everyone,
The other day a client gave me her Windows Vista laptop that was in very bad shape. After a quick diagnosis it was apparent that the machine needed a new hard drive. I popped in a nice new 2.5″ Western Digital drive, inserted my Windows Vista Home Premium Upgrade disc (into the CD/DVD ROM drive), rebooted the computer, and we were “off to the races”. This installation was going to be a “snap”.
Not quite!!
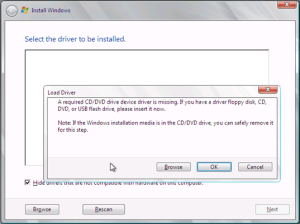
After the first two initial screens came up (1: selections for language, time, currency format, and keyboard layout 2: repair a previous installation or “Install Now”), I got the following message:
A required CD/DVD drive device driver is missing. If you have a driver floppy disk, CD, DVD, or USB flash drive, please insert it now.
When I saw this message this is what I did:
1) I hooked up an external USB CD/DVD ROM (like this one) to one of the USB ports,
2) Removed the Vista installation disc from the computers CD/DVD ROM drive,
3) Inserted the Vista installation disc into the external DVD drive ( didn’t have to reboot),
4) Sat back and watched the Vista installation proceed without a hitch! Great stuff!
I’m sure that this same procedure will work with Windows 7 also.
Professor Randy says: Don’t get “bent out of shape” when you see the “A required CD/DVD drive device is missing….” message. Choose the easy way out and continue the installation by inserting the disc into a portable USB external DVD drive.
Tags:
install windows using an external usb drive,
load driver during windows installation,
required cd/dvd drive device is missing
July 23rd, 2013 at 9:07 pm

Hello everyone,
In this March post I told you about a great program that will show you all of your computers third party program vulnerabilities, and then download and install the latest vulnerability fixes. Great stuff!
Speaking of vulnerabilities, here is a chart of the non-MS patches that affect Windows platforms in the present month of July. Get updated asap!
July 2013
|
|
|
|
Identifier
|
Vendor/Product
|
Product Version Affected
|
Date Released by Vendor
|
Vulnerability Info
|
Vendor
Severity / Our Recommendation
|
|
APSB13-17
|
Adobe Flash Player
|
For Windows,
11.7.700.224 and earlier
|
7/9/2013
|
Multiple vulnerabilities
|
Critical: Patch within 72 Hours
|
|
APSB13-18
|
Adobe Shockwave Player
|
For Windows,
12.0.2.122 and earlier
|
7/9/2013
|
Remote code via memory corruption
|
Critical: Patch within 72 Hours
|
|
APSB13-19
|
Adobe ColdFusion
|
ColdFusion 10
|
7/9/2013
|
Attacker can call ColdFusion Components (CFC) public methods via WebSockets.
|
Critical: Patch within 72 Hours
|
|
27.0.1500.68
|
Google Chrome
|
For Windows before
27.0.1500.68
|
7/11/2013
|
Multiple high risk vulnerabilities fixed
|
Critical: upgrade to latest release
|
|
22.0
|
Mozilla Firefox
|
Before 22
|
6/25/2013
|
Multiple High risk vulnerabilties fixed
|
Critical: upgrade to latest release
|
|
17.0.7
|
Mozilla Thunderbird
|
Before 17.0.7
|
6/25/2013
|
Multiple High risk vulnerabilties fixed
|
Critical: upgrade to latest release
|
|
2.19
|
Mozilla SeaMonkey
|
Before 2.19
|
7/2/2013
|
Multiple High risk vulnerabilties fixed
|
Critical: upgrade to latest release
|
Tags:
non-microsoft patches for july 2013,
third party program updates for July 2013











