May 27th, 2014 at 6:07 pm
Hello everyone,
It is not enough anymore to just keep your Operating System updated and patched. Many third party (non Microsoft) programs need constant updating also. If these programs are left unpatched, your system is wide open to attack. Most of the malware attacks that I see in my computer repair business are due to outdated versions of third party applications like the ones shown below. Please take a look at the May 2014 third party updates, and get the most recent versions as soon as you can. I have linked to three great automatic updaters. Check them out!
|
Randy The Tech Professor
|
Please check out these links:
http://www.kcsoftwares.com/?sumo
http://cleansofts.org/view/update-notifier.html
http://secunia.com/vulnerability_scanning/personal/ |
|
Identifier
|
Vendor/Product
|
Product Version Affected
|
Date Released by Vendor
|
Vulnerability Info
|
Vendor
Severity / My Recommendation
|
|
APSB14-11
|
Adobe Illustrator
|
Windows CS6 (Subscription) 16.2.0 and earlier
(Non- Subscription)
16.0.3 and earlier
Mac CS6 (Subscription) 16.2.1 and earlier
(Non-Subscription) 16.0.4 and earlier
|
5/13/2014
|
Arbitrary Code Execution
|
Critical: Priority 3/ Upgrade at admin’s discretion
|
|
APSB14-14
|
Adobe Flash
|
Windows/Mac 13.0.0.206 and earlier
Linux 11.2.202.356 and earlier
|
5/13/2014
|
Arbitrary Code Execution
|
Critical: Priority 1/ Upgrade within 72 hours
|
|
APSB14-14
|
Adobe Air
|
Windows/Mac 13.0.0.83
and earlier
|
5/13/2014
|
Arbitrary Code Execution
|
Critical: Priority 3/ Upgrade at admin’s discretion
|
|
APSB14-15
|
Adobe Reader/Acrobat
|
Windows/Mac Reader/Acrobat XI 11.0.0.6 and earlier
Reader/Acrobat X 10.1.9 and earlier
|
5/08/2014
|
Arbitrary Code Execution, Denial of Service
|
Critical: Priority 1/ Upgrade within 72 hours
|
|
iTunes 11.2
|
Apple
|
Windows before 11.2
|
5/15/2014
|
Security Bypass
|
Recommended
|
|
iTunes 11.2.1
|
Apple
|
Mac before 11.2.1
|
5/16/2014
|
Security Bypass
|
Recommended
|
|
35.0.1916.114
|
Chrome
|
Windows/Mac/Linux before 54.0.1916.114
|
5/20/2014
|
Information Disclosure, Denial of Service, Cross Site Scripting, UI Spoofing
|
Recommended: Upgrade after testing
|
|
29/ESR 24.5
|
Mozilla Firefox
|
Before Firefox 29/ESR 24.5
|
4/29/2014
|
Arbitrary Code Execution, Denial of Service, Cross Site Scripting, Security Bypass
|
Recommended: Upgrade after testing
|
|
24.5
|
Mozilla Thunderbird
|
Before Thunderbird 24.5
|
4/29/2014
|
Arbitrary Code Execution, Denial of Service, Cross Site Scripting, Security Bypass
|
Recommended: Upgrade after testing
|
|
2.26
|
Mozilla Seamonkey
|
Before Seamonkey 2.26
|
4/29/2014
|
Arbitrary Code Execution, Denial of Service, Cross Site Scripting, Security Bypass
|
Recommended: Upgrade after testing
|
Tags:
may 2014 third party program updates,
patch non-microsoft programs,
third party program updates
May 5th, 2014 at 7:51 pm

Hello everyone
I received this email today. Looks good doesn’t it? Well, it’s a total scam! If you get an email like this do not even think about opening the attachment. Hackers will try to use scare tactics on you so that you click without thinking. Stay calm and don’t be fooled!
Keep in mind that scammers often use scare tactics to try to get you to react without thinking. – See more at: http://www.scamtrends.com/tag/paypal-review-department/#sthash.ZNE07DIU.dpuf
Keep in mind that scammers often use scare tactics to try to get you to react without thinking. – See more at: http://www.scamtrends.com/tag/paypal-review-department/#sthash.ZNE07DIU.dpuf
Keep in mind that scammers often use scare tactics to try to get you to react without thinking. – See more at: http://www.scamtrends.com/tag/paypal-review-department/#sthash.ZNE07DIU.dpuf
Dear Valued Customer,
Our Account Protection System recently detected an issue with your account.
There was an unusual activity on the credit card linked to your PayPal
account. Our security team suspects that an unauthorized user tried to access
your account without your consent.
Your account have been temporarily limited. We understand this may be
frustrating and inconvenient for you.
What to do next:
Please download the attachment in this email and simply open it so that
you are able to proceed with the verification process. Please fill in the required
fields after you have opened the attachment.
We apologize for any inconvenience that may have been caused.
Sincerely,
Copyright © 1999-2014 PayPal. All rights reserved.
Best wishes,
Randy Knowles
Tags:
paypal account review scam attempt,
paypal email scam
April 28th, 2014 at 8:16 pm
 Hello everyone,
Hello everyone,
In this March post (2013), I told you about three great programs that will show you all of your computers third party program vulnerabilities, and then download and install the latest vulnerability fixes. Great stuff!
Speaking of vulnerabilities, here is a chart of the non-MS patches that affected Windows platforms in the current month of April 2014. Get updated asap!
7u55
Oracle Java SE, JavaFX, Java SE Embedded
SE 7u51 and earlier, SE 6u71 and earlier, SE 5.0u61 and earlier, SE Embedded 7u51 and earlier, JavaFX 2.2.51 and earlier
4/18/2014
Data Integrity
Critical: Upgrade to latest release
APSB14-09
Adobe Flash Player
Windows/Mac 12.0.0.77 and earlier Linux 11.2.202.346 and earlier
4/8/2014
Arbitrary Code Execution, Cross Site Scripting, Security Bypass
Critical Priority 1/ Upgrade within 72 hours
APSB14-09
Adobe Air
Android 4.0.0.1628 and earlier
4/8/2014
Arbitrary Code Execution, Security Bypass
Critical: Priority 3/ Upgrade at admin’s discretion
APSB14-12
Adobe Reader Mobile
Android 11.1.3 and earlier
4/14/2014
Arbitrary Code Execution
Critical: Priority 2/ Upgrade within 30 days
34.0.1847.131 and 34.0.1847.132
Google Chrome
Windows/Mac before 34.0.1847.131 Linux before 34.0.1847.132
4/24/2014
Security Bypass, Denial of Service
Recommended: Upgrade after testing
Best wishes,
Randy Knowles
Tags:
non-windows patches for april 2014,
patch third party programs,
third party program updates
April 19th, 2014 at 10:22 am
Hello everyone,
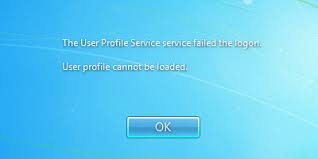
I got a call the other day from a frantic client. He was an experienced artist and he could not logon to his Windows account. His user account was not accepting his password. Had he lost all of his files?
I went over to his house with my favorite password crackers thinking that it was a password issue. As soon as I saw the dreaded error message “The User Profile Service failed the logon”, I knew that it was not a password problem. This was a bug that required a registry fix.
Here is what I did to fix the issue:
- Boot into safe mode
- Click on the start button, and type “regedit” into the search bar.
- Hit enter to open regedit.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList
- You’ll see two “S-1-5….” folders with long names. One of them will end in “.bak”
- Rename the one that does not end in “.bak” to (long string of numbers) “.bad” or “.old”
- Remove the “.bak” from the other one.
- With this folder selected, double click RefCount and type 0 and then click OK.
- With this folder selected, double click State and type 0 and then click OK.
- Reboot the machine, and it should be fixed.
After the machine rebooted, the client typed in his original password and the logon was successful. He looked at me with an expression of relief and gratitude, shook my hand profusely, and paid me a nice fee. I think I’ve just made a customer for life!
Best wishes,
Randy The Tech Professor
Tags:
can't logon to the user account,
registry fix for user accounts,
the user profile service failed the logon
March 24th, 2014 at 9:58 pm

Hello everyone,
In this March post (one year ago), I told you about three great programs that will show you all of your computers third party program vulnerabilities, and then download and install the latest vulnerability fixes. Great stuff!
Speaking of vulnerabilities, here is a chart of the non-MS patches that affected Windows platforms in the current month of March 2014. Get updated asap!
|
Identifier
|
Vendor/Product
|
Product Version Affected
|
Date Released by Vendor
|
Vulnerability Info
|
Vendor
Severity / My Recommendation
|
|
iOS 7.1
|
Apple
|
BeforeiOS 7.1
|
3/10/2014
|
Denial of Service, Data Integrity, Security Bypass, Information Disclosure
|
Recommended
|
|
APSB14-08
|
Adobe Flash Player
|
Windows/Mac 12.0.0.70and earlier Linux 11.2.202.341 and earlier
|
3/11/2014
|
Security Bypass, Information Disclosure
|
Important: Priority 2/ Upgrade within 30 days if possible
|
|
APSB14-10
|
Adobe Shockwave Player
|
Windows/Mac 12.0.9.149and earlier
|
3/13/2014
|
Arbitrary Code Execution
|
Critical: Priority 2/ Upgrade within 30 days if possible
|
|
30.0.1750.154
|
Chrome
|
Windows before 30.0.1750.154 Mac/Linux before 30.0.1750.152
|
3/14/2014
|
Arbitrary Code Execution, Information Disclosure
|
Recommended: Upgrade after testing
|
|
28 ESR 24.4
|
Mozilla Firefox
|
BeforeFirefox 28 and ESR 24.4
|
3/18/2014
|
Arbitrary Code Execution, Privilege Escalation, Information Disclosure
|
Recommended: Upgrade after testing
|
|
24.4
|
Mozilla Thunderbird
|
Before Thunderbird 24.4
|
3/18/2014
|
Arbitrary Code Execution, Privilege Escalation, Information Disclosure
|
Recommended: Upgrade after testing
|
|
2.25
|
Mozilla Seamonkey
|
Before Seamonkey 2.25
|
3/18/2014
|
Arbitrary Code Execution, Privilege Escalation, Information Disclosure
|
Recommended: Upgrade after testing
|
Tags:
non-microsoft patches for march 2014,
third party program updates for march 2014
March 14th, 2014 at 11:07 pm
Hello everyone,
I believe that computer repair techs will always be in demand. The Internet is so full of different types of malware that only a very savvy user can avoid it. Many of the attacks now are through browser hijackers, add-ons and extensions. Consider what just happened to me:
I got a call from a client who said that her laptop was “running slow”. Once I got the laptop to my shop and turned it on, I was surprised that it was even running at all. I could have held an actual clinic for anyone interested in learning how to identify and remove malware. Consider what I identified and removed (a couple of these items are not actually malware, but do slow the computer down and can be replaced with more effective programs):
RegClean Pro, XFINITY Toolbar, Windows Live Toolbar, VideoDownloadConverter Firefox Toolbar, Utility Chest Toolbar, TotalRecipe Toolbar, TelevisionFanatic Firefox Toolbar, Shop To Win, Search Protect, Recipe Hub Toolbar, PricePeep for I.E., MyPC Backup, My Web Search (Popular Screensavers), McAfee Security Scan Plus, Marine Aquarium Lite Toolbar, I Want This, Homepage by Mindspark Interactive, Google Toolbar for I.E., DesktopWeatherAlerts, Crawler Toolbar, Constant Guard Protection Suite, DiskMax 4.56, Coupon Alert, Coupon Printer for Windows, Bing Bar, Babylon Object Installer, Advanced System Protector, Adobe Reader, Norton PC Checkup, Norton Security Suite, Visual Bee.
That’s a lot of “junk” on one laptop. There were also outdated versions of Flash, Java and Shockwave Player. I replaced Adobe Reader with Sumatra PDF, reset System Restore, installed Microsoft Security Essentials, ran Defraggler, changed some Power Options, and had previously ran CCleaner, PureRa, Revo Uninstaller Junk Files Remover, and Gould CleanUp. For good measure I ran CrystalDiskInfo to check the hard drive.
When I returned the laptop the client was amazed at how well it was running and could not understand “how all of that junk got on her computer”. This lack of understanding is why I believe that computer repair techs will always be in demand.
Tags:
malware removal,
types of malware
February 24th, 2014 at 9:02 pm
 Hello everyone,
Hello everyone,
In this March post I told you about three great programs that will show you all of your computers third party program vulnerabilities, and then download and install the latest vulnerability fixes. Great stuff!
Speaking of vulnerabilities, here is a chart of the non-MS patches that affected Windows platforms in the current month of February 2014. Get updated asap!
|
Identifier
|
Vendor/Product
|
Product Version Affected
|
Date Released by Vendor
|
Vulnerability Info
|
Vendor
Severity / My Recommendation
|
|
APSB14-07
|
Adobe Flash Player
|
Windows/Mac 12.0.0.44 and earlier Linux 11.2.202.336 and earlier
|
2/20/2014
|
Arbitrary Code Execution
|
Critical: Priority 1/ Upgrade within 72 hours if possible
|
|
APSB14-07
|
Adobe Air
|
Windows/Mac/Android 3.9.0.1390 and earlier
|
2/20/2014
|
Arbitrary Code Execution
|
Critical: Priority 3/Upgrade at admin’s discretion
|
|
APSB14-06
|
Adobe Shockwave Player
|
Windows/Mac 12.0.7.148 and earlier
|
2/11/2014
|
Arbitrary Code Execution, Denial of Service
|
Critical: Priority 1/ Upgrade within 72 hours if possible
|
|
iOS 7.0.6/6.1.6
|
Apple
|
Before iOS 7.06 and before iOS 6.1.6
|
2/21/2014
|
Data Integrity, Information Disclosure
|
Recommended
|
|
33.0.1750.117
|
Chrome
|
Windows/Mac/Linux Before 33.0.1750.117
|
2/20/2014
|
Arbitrary Code Execution, Denial of Service, Security Bypass, Information Disclosure
|
Recommended: Upgrade after testing
|
|
27 ESR 24.3
|
Mozilla Firefox
|
Before Firefox 27 and ESR 24.3
|
2/4/2014
|
Arbitrary Code Execution, Denial of Service, Security Bypass, Information Disclosure
|
Recommended: Upgrade after testing
|
|
24.3
|
Mozilla Thunderbird
|
Before Thunderbird 24.3
|
2/4/2014
|
Arbitrary Code Execution, Information Disclosure
|
Recommended: Upgrade after testing
|
|
2.24
|
Mozilla SeaMonkey
|
Before 2.24
|
2/4/2014
|
Arbitrary Code Execution, Denial of Service, Security Bypass, Information Disclosure
|
Recommended: Upgrade after testing
|
Best wishes,
Randy The Tech Professor
Tags:
patch non-microsoft programs,
update third party programs,
vulnerable third party software
January 27th, 2014 at 10:17 pm

Hello everyone,
In this March post I told you about three great programs that will show you all of your computers third party program vulnerabilities, and then download and install the latest vulnerability fixes. Great stuff!
Speaking of vulnerabilities, here is a chart of the non-MS patches that affected Windows platforms in the past month of January 2014. Get updated asap!
|
Identifier
|
Vendor/Product
|
Product Version Affected
|
Date Released by Vendor
|
Vulnerability Info
|
Vendor
Severity / My Recommendation
|
|
APSB14-01
|
Adobe Reader / Adobe Acrobat
|
Windows/Mac XI 11.0.05 and earlier / X 10.1.8 and earlier
|
1/14/2014
|
Arbitrary Code Execution or Denial of Service
|
Critical: Priority 1/ Upgrade within 72 hours if possible
|
|
APSB14-02
|
Adobe Flash Player
|
Windows/Mac 11.9.900.170 and earlier / Linux 11.2.202.332 and earlier
|
1/14/2014
|
Arbitrary Code Execution
|
Critical: Priority 1/ Upgrade within 72 hours if possible
|
|
APSB14-02
|
Adobe Air
|
Windows/Mac 3.9.0.1380 and earlier
|
1/14/2014
|
Arbitrary Code Execution
|
Critical: Priority 3/ Upgrade at admin’s discretion
|
|
APSB14-03
|
Adobe Digital Editions
|
Windows/Mac 2.01
|
1/22/2014
|
Arbitrary Code Execution
|
Critical: Priority 3/ Upgrade at admin’s discretion
|
|
11.1.4
|
iTunes
|
Windows/Mac
Prior to 11.1.4
|
1/22/2014
|
Arbitrary Code Execution, Denial of Service
|
Recommended
|
|
5.1/2.1
|
Pages
|
OSX/iOS prior to Pages 5.1 or 2.1
|
1/23/2014
|
Arbitrary Code Execution, Denial of Service
|
Recommended
|
|
7u51
|
Oracle Java SE, Java FX, Java SE Embedded
|
SE 7u45 and earlier, SE 6u65 and earlier, SE 5.0u55 and earlier, SE Embedded 7u45 and earlier, JavaFX 2.2.45 and earlier
|
1/14/2014
|
36 security vulnerabilities fixed of which 34 may be remotely exploitable without authentication
|
Critical: Upgrade to latest release
|
|
32.0.1700.76and 32.0.1700.77
|
Chrome
|
Windows before 32.0.1700.76 Linux/Mac Before 32.0.1700.77
|
1/14/2014
|
Denial of service, improper sync, address bar spoofing
|
Recommended: Upgrade after testing
|
Best wishes,
Randy The Tech Professor
Tags:
non-microsoft program patches for January 2014,
third party security patches,
update third party programs
January 20th, 2014 at 11:41 am
 Hello everyone,
Hello everyone,
The SSD (Solid State Drive) is the greatest invention since “sliced bread”. Installing an SSD can cut boot times down to below ten seconds and open programs so fast that your head will swim! The greatest single speed upgrade for your computer is without doubt the installation of a Solid State Drive.
Yet many people install an SSD, and see little or no speed increase. What’s up?
Take a look at this beautiful Solid State Drive: A super fast SSD indeed, but will your computer be able to utilize this speed? If your computer motherboard does not have the adequate bus speed, then you will never see the true benefits of your SSD.
It all depends upon what version of SATA ports are on your motherboard. If your motherboard does not have high speed SATA connections (SATA3 at 6Gb/s), then your I/O bus will bog down well before you can experience the speed of the SSD.
If you connect a 6Gb/s capable SSD to a SATA2 port then you will only get 3Gb/s. If you connect a 6Gb/s SSD to a SATA1 port, then your throughput will only be 1.5Gb/s.
If you have an older computer/motherboard and you want to enjoy the incredible speed of an SSD drive, you may be able to add a SATA 3 card. Even better would be to get a PCIe card and connect the SSD to the PCIe bus instead of the SATA bus. When installing an expansion card, please make sure that your motherboard is compatible.
Professor Randy says: An SSD will change your computing life! Just make sure that your motherboard has the correct ports in order to take full advantage of the drive.
Tags:
sata bus,
solid state drive optimization,
ssd on PCIe bus
January 8th, 2014 at 10:02 pm
Hello everyone,
In part 1 of this post I named sixteen malicious programs/items that are secretly installing themselves to the Google Chrome, Mozilla Firefox, and Microsoft Internet Explorer browsers. I talked about another well known one here.
These malicious items cause annoying pop-ups, pop-unders, banners, and coupons. They change Windows start-up settings and Internet browser settings. They change the homepage, redirect browser searches, and generally make Internet browsing experience hell! Ultimately they will ruin the computers functionality!
In todays post I would like to show you how to get rid of these unwanted, unwelcome, and infectious browser plug-ins.
1) Some, but not all of these “crap entities” will show up on your computer as installed programs. Uninstall them completely using Revo Uninstaller (free version). Revo Uninstaller is a much faster and more powerful alternative to “Windows Programs and Features (Add or Remove Programs)” applet! It has very powerful features to uninstall and remove programs.
2) The rest of these “crap entities” will show up in your browers as plug-ins/extensions. You must remove them from each browser that you have on your machine. This is how you do it:
A) Firefox (make sure your Menu Bar is enabled)
Tools>Add-ons>Extensions>Remove
B) Internet Explorer (enable Menu Bar)
Tools>Manage add-ons>Toolbars and Extensions>Highlight the plug-in>Disable
C) Chrome (click on the three horizontal bars in top right corner)
Tools>Extensions>Remove from Chrome (click on the trash can)
Professor Randy says: Don’t allow these unscrupulous programs to usurp your computer user joy! You are in control of your machine, not them! If they do manage to attach themselves to your browser, eradicate them fully using the above method.
Tags:
remove malicious browser add-ons,
remove malicious browser highjackers,
remove malicious extensions,
remove malicious toolbars












